Disable:
bcdedit /set {default} bootstatuspolicy ignoreallfailures
Re-enable:
bcdedit /set {default} bootstatuspolicy displayallfailures
Disable Windows 7 autorepair
- Posted on
- – Make a comment on Disable Windows 7 autorepair
So you don't have to reinvent the wheel.
Disable:
bcdedit /set {default} bootstatuspolicy ignoreallfailures
Re-enable:
bcdedit /set {default} bootstatuspolicy displayallfailures
I just found back an old note about using iptables in combination with dyndns to open up access from a remote location. For instance, if you have a laptop that you take everywhere and you want to connect to your home or office. The script the other site suggested was broken, so let's write a new one.
Create a new chain in the firewall where we can plug in the dynamic rules. On my Fedora machine, the firewall is located in /etc/sysconfig/iptables. I added the bold lines to this example.
*nat
:PREROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
<b>:DYNAMIC - [0:0]
-A INPUT -j DYNAMIC</b>
-A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
#!/bin/bash HOSTNAME=myname.dyndns.org CHECK_INTERVAL=60 #once a minute /sbin/iptables -F DYNAMIC #flush all existing rules IP="" #initialize $IP while [ true ]; do OIP=$IP IP=$(host $HOSTNAME | grep -iE "[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+" |cut -f4 -d' '|head -n 1) if [ "$OIP" != "$IP" -a "$IP" != "" ]; then echo "Changing ip to $IP" /sbin/iptables -F DYNAMIC #flush all old rules /sbin/iptables -I DYNAMIC -s $IP -j ACCEPT #the new rule fi sleep $CHECK_INTERVAL done |
In this case, the firewall accepts all traffic from $IP, but of course you could restrict it to 1 port. Also, I focussed on IPv4, but you could easily rewrite this script to IPv6 using ip6tables. I saved the file to /usr/local/bin/dynfirewall.sh
I'd prefer running the script from inittab, but since Fedora doesn't work like this anymore, I put the following line in /etc/rc.d/rc.local:
/usr/local/bin/dynfirewall.sh >>/var/log/dynfirewall 2>>/var/log/dynfirewall & |
Please don't forget the ampersand at the end to fork the script!!
© GeekLabInfo iptables and dynamic DNS is a post from GeekLab.info. You are free to copy materials from GeekLab.info, but you are required to link back to http://www.geeklab.infoLast weekend, one of my 3com 4250T switches stopped functioning. I used a multimeter and the fuse seems okay, but it's dead as a doorknob. Since my switches are stacked to one virtual unit, I bought a second hand 4250T to replace the broken one.
As often with second hand crap, this switch contained settings from the last location. Including an unknown password.
Fortunately, the switches have a recovery mode (which can also be disabled, so below instructions may not work on another switch).
I connected the switch to a RS232 port using a null-modem cable. If you know the switches IP, you can also use telnet.
Login: recover
Password: recover*** Password Recovery Mode ***
The administrative password will be cleared if a hard reset operation is
carried out on the device within 30 seconds.If a hard reset operation is not carried out during this period, the device
will return to the CLI login promptcountdown = 30...29...28...
Pull the plug of the switch before the countdown reaches 0. When you boot it again, you can login using the default user "admin" and simply press enter for 'password'.
This manual may work on:
3COM SuperStack 3 4400
3COM SuperStack 3 4900
3COM SuperStack 3 4924
3COM SuperStack 3 4950
3COM SuperStack 3 4300
3COM SuperStack 3 Webcache
3COM SuperStack 3 Webcache 1000
3COM SuperStack 3 Webcache 3000
3COM SuperStack 4200 series
3COM SuperStack 3 Switch 4250T
3COM SuperStack 3 Switch 4226T
3COM Switch 4050
3COM Switch 4060
3COM 3C16115
3COM 3C16116
Today, my dear wife asked me to help her with her facebook addiction. She wondered if I could block facebook, gmail, some news sites and more during her work hours. Sure, I can. And since she's running Linux as well, I could even do it on her own computer.
Squid is a FLOSS proxy server that runs on Linux and several other sytems. It's capable of filtering and behaving transparently. Just what we need.
yum -y install squid
acl manager proto cache_object
acl localhost src 127.0.0.1/32 ::1
acl to_localhost dst 127.0.0.0/8 0.0.0.0/32 ::1# Example rule allowing access from your local networks.
# Adapt to list your (internal) IP networks from where browsing
# should be allowed
acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machinesacl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT# Here I define the times and what file contains the rules
acl playtime1 time SMTWHFA 8:30-9:30
acl playtime22 time SMTWHFA 16:00-17:00
acl addiction url_regex -i "/etc/squid/addiction"# Only allow cachemgr access from localhost
http_access allow manager localhost
http_access deny manager# Deny requests to certain unsafe ports
http_access deny !Safe_ports# Deny CONNECT to other than secure SSL ports
http_access deny CONNECT !SSL_ports# We strongly recommend the following be uncommented to protect innocent
# web applications running on the proxy server who think the only
# one who can access services on "localhost" is a local user
#http_access deny to_localhost#
# INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS
## The next few lines actually do the work
http_access allow playtime1 addiction
http_access allow playtime2 addiction
http_access deny addiction
# If this ACL is triggered, show the user the WORKONLY error message.
deny_info WORKONLY addiction# Example rule allowing access from your local networks.
# Adapt localnet in the ACL section to list your (internal) IP networks
# from where browsing should be allowed
http_access allow localnet
http_access allow localhost# And finally deny all other access to this proxy
http_access deny all# Squid normally listens to port 3128
# I added the word "transparent", so squid behaves a little different:
# it makes itself transparent. NOTE TO SELF: This is the line you're
looking for. Used to be httpd_accel_uses_host_header in squid 2http_port 3128 transparent
# We recommend you to use at least the following line.
hierarchy_stoplist cgi-bin ?# Uncomment and adjust the following to add a disk cache directory.
#cache_dir ufs /var/spool/squid 100 16 256# Leave coredumps in the first cache dir
coredump_dir /var/spool/squid# Add any of your own refresh_pattern entries above these.
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320# Don't show squid to the outside world
forwarded_for delete# I don't need to log what she's doing
access_log none
# Nor do i need icap logs
icap_log none
# And i don't want to know what is stored in cache
cache_store_log none
# To not break web apps, I don't want caching either
cache deny all
Type a list of blocked websites in /etc/squid/addiction. You can use complete urls, domains or even just words. Ie. "facebook" blocks http://www.facebook.com, but also http://wikipedia.org/wiki/facebook
In the configuration, I put: deny_info WORKONLY addiction. This means that I can leave the user a message in /usr/share/squid/errors/templates/WORKONLY and /usr/share/squid/errors/en/WORKONLY. Since it's my wife's PC, I decided to leave her a sweet message :-D
I could configure her Firefox to use the proxy. But then she'd use Google Chrome or Konqueror to surf the web. And she could turn the proxy off. So I need to catch all http-traffic that did not pass squid. I used iptables:
#Allow user 'root' to surf the web, for yum update etc. iptables -t nat -A OUTPUT -m tcp -p tcp --dport 80 -m owner --uid-owner root -j RETURN # Allow user 'squid' to pass on http requests iptables -t nat -A OUTPUT -m tcp -p tcp --dport 80 -m owner --uid-owner squid -j RETURN # Redirect all other traffic to the proxy. iptables -t nat -A OUTPUT -m tcp -p tcp --dport 80 -j REDIRECT --to-ports 3128 |
On my SBS 2003 server, I wanted to know when a user was created. This info is extracted with ldifde
ldifde -d OU=SBSUsers,OU=Users,OU=MyBusiness,DC=xxx,DC=yyy -l whencreated -r "(ObjectCategory=user)" -f usercreationdate.txt |
A file usercreationdate.txt is now created with the requested report.
© GeekLabInfo List user creation date for Active Directory users is a post from GeekLab.info. You are free to copy materials from GeekLab.info, but you are required to link back to http://www.geeklab.info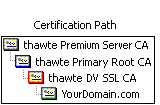 Normal "single root" certs are only certified by one single parent which is recognised by clients immediately. Chained certs on the other side are signed by a parent which itself is signed by another parent. This effectively makes your cert a "grandchild" of the CA root. In the image attached you'll see a cert that is chained by two intermediate certs.
Normal "single root" certs are only certified by one single parent which is recognised by clients immediately. Chained certs on the other side are signed by a parent which itself is signed by another parent. This effectively makes your cert a "grandchild" of the CA root. In the image attached you'll see a cert that is chained by two intermediate certs.
The several server software distributions require different types of configuration. This page is not telling you how to set up ssl for your software, I'm just telling how to use chained certs with the different programs.
Apache has quite some SSL functionality on board. I'm not gonna discuss it all, just want to say that the words you're looking for are:
SSLCertificateFile [path to crt file here]
SSLCertificateKeyFile [path to key file here]
SSLCACertificateFile [path to intermediate ca certs bundle here]
I downloaded the intermediate CA certs from my SSL provider: https://search.thawte.com/support/ssl-digital-certificates/index?page=content&id=AR1371 . Your SSL provider has a page with their own intermediate CA certs.
My PureFTPd key and cert are all located in /etc/pure-ftpd/pure-ftpd.pem. In order to make ftp clients accept the SSL cert, i performed the following steps:
My dovecot SSL key is located in /etc/pki/dovecot/private/dovecot.pem and my SSL cert is /etc/pki/dovecot/certs/dovecot.pem. In order to make email clients accept the SSL cert, i performed the following steps:
My postfix key and cert are all located in /etc/postfix/ssl/smtpd.pem.
In order to make email clients accept the SSL cert, i performed the following steps:
An EAN13 barcode has a built-in checksum to help cash registers discover damaged barcodes. You can easily check these checksums by hand.
| Standard | Digit positions | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| EAN-8 | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | |||||||||||
| EAN-12 | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | N9 | N10 | N11 | N12 | |||||||
| EAN-13 | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | N9 | N10 | N11 | N12 | N13 | ||||||
| EAN-14 | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | N9 | N10 | N11 | N12 | N13 | N14 | |||||
| SSCC | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | N9 | N10 | N11 | N12 | N13 | N14 | N15 | N16 | N17 | N18 | |
| Step 1: Multiply value of each position by | |||||||||||||||||||
| x3 | x1 | x3 | x1 | x3 | x1 | x3 | x1 | x3 | x1 | x3 | x1 | x3 | x1 | x3 | x1 | x3 | |||
| Step 2: Add results together to create sum | |||||||||||||||||||
| Step 3: Subtract the sum from nearest equal or higher multiple of ten = Check Digit | |||||||||||||||||||
The following table gives an example to illustrate how a Check Digit is calculated:
| Pos | N1 | N2 | N3 | N4 | N5 | N6 | N7 | N8 | N9 | N10 | N11 | N12 | N13 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Number without Check Digit | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 1 | 2 | 3 | - |
| Step 1: Multiply | x | x | x | x | x | x | x | x | x | x | x | x | - |
| by | 1 | 3 | 1 | 3 | 1 | 3 | 1 | 3 | 1 | 3 | 1 | 3 | - |
| Step 2: Add results | = | = | = | = | = | = | = | = | = | = | = | = | - |
| to create sum | 1 | 6 | 3 | 12 | 5 | 18 | 7 | 24 | 9 | 3 | 2 | 9 | = 91 |
| Step 3: Subtract the sum from nearest equal or higher multiple of ten = 100-99 = 1 | |||||||||||||
| Number with Check Digit | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 1 | 2 | 3 | 1 |
My PHP code to check the CRC code:
function ean13_check_digit($digits){ $digits=preg_split("//",$digits,-1,PREG_SPLIT_NO_EMPTY); $a=$b=0; for($i=0;$i<6;$i++){ $a+=(int)array_shift($digits); $b+=(int)array_shift($digits); } $total=($a*1)+($b*3); $nextten=ceil($total/10)*10; return $nextten-$total==array_shift($digits); } echo ean13_check_digit('1234567891231')?"good":"wrong"; echo ean13_check_digit('1234567891232')?"good":"wrong"; echo ean13_check_digit('1234567891233')?"good":"wrong"; echo ean13_check_digit('1234567891234')?"good":"wrong"; echo ean13_check_digit('1234567891235')?"good":"wrong"; echo ean13_check_digit('1234567891236')?"good":"wrong"; echo ean13_check_digit('1234567891237')?"good":"wrong"; |